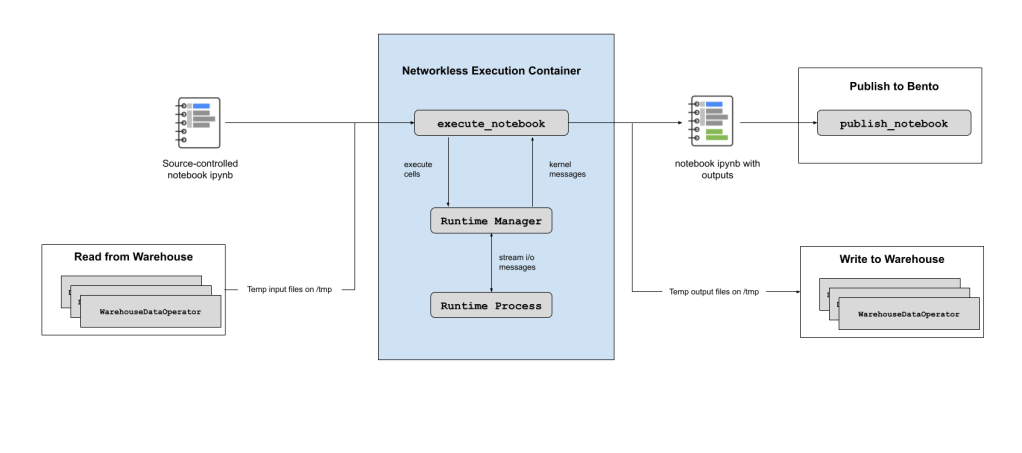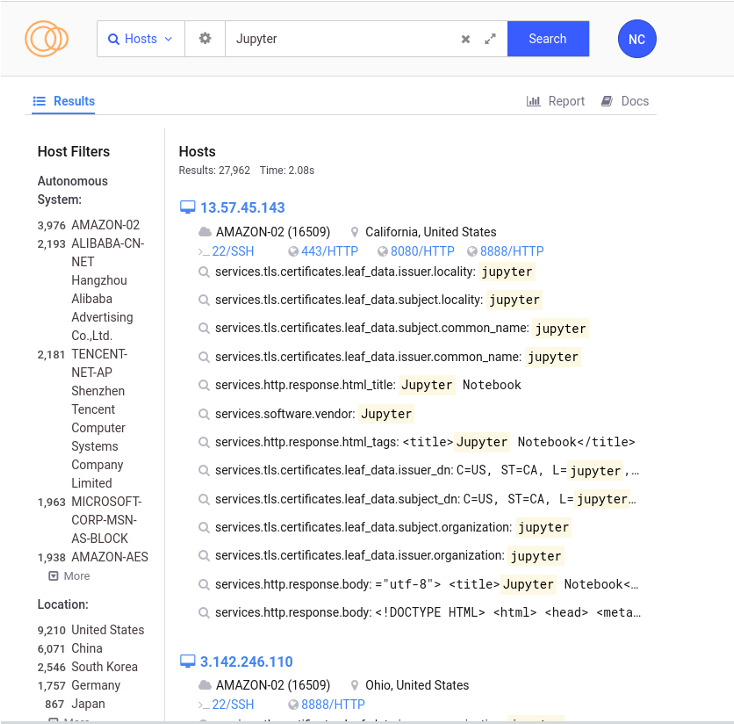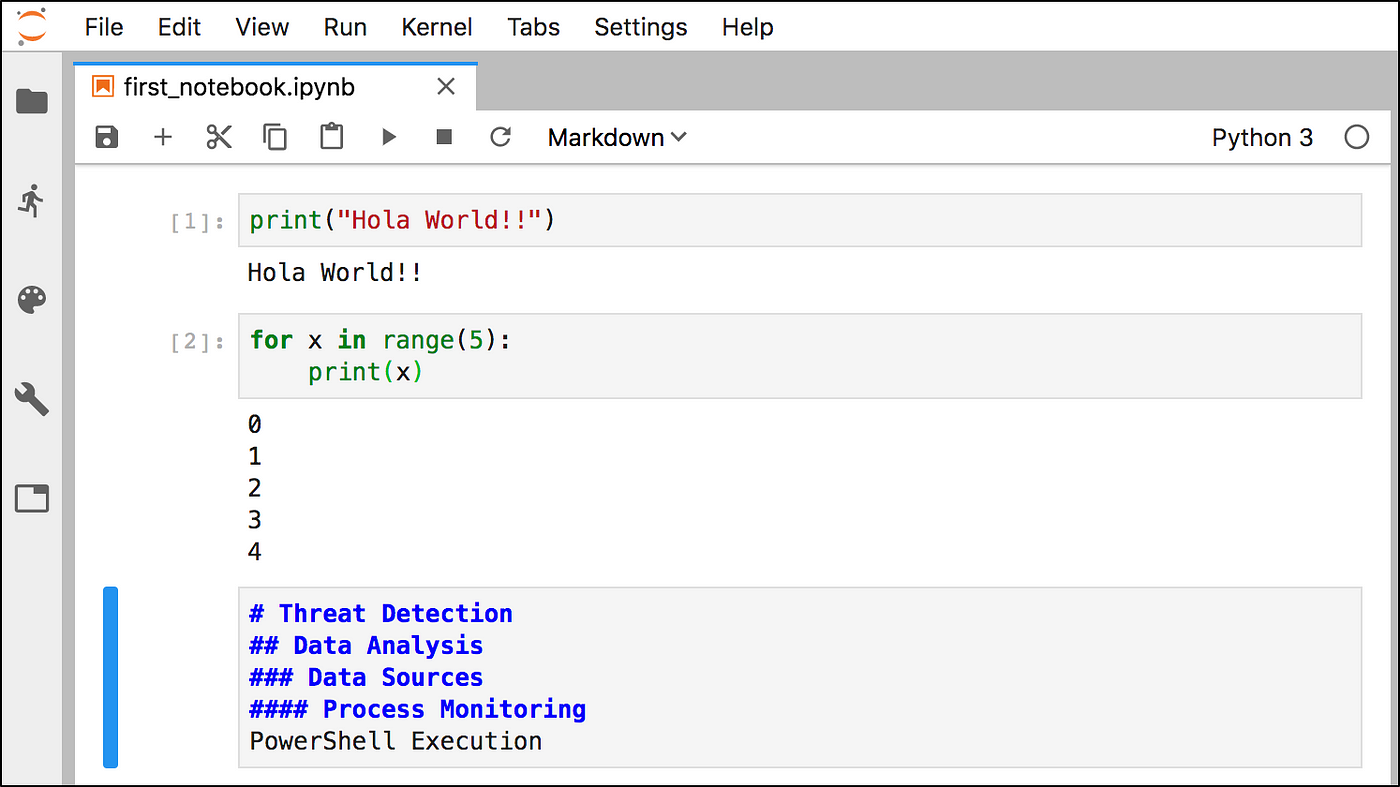
Threat Hunting with Jupyter Notebooks— Part 1: Your First Notebook 📓 | by Roberto Rodriguez | Posts By SpecterOps Team Members
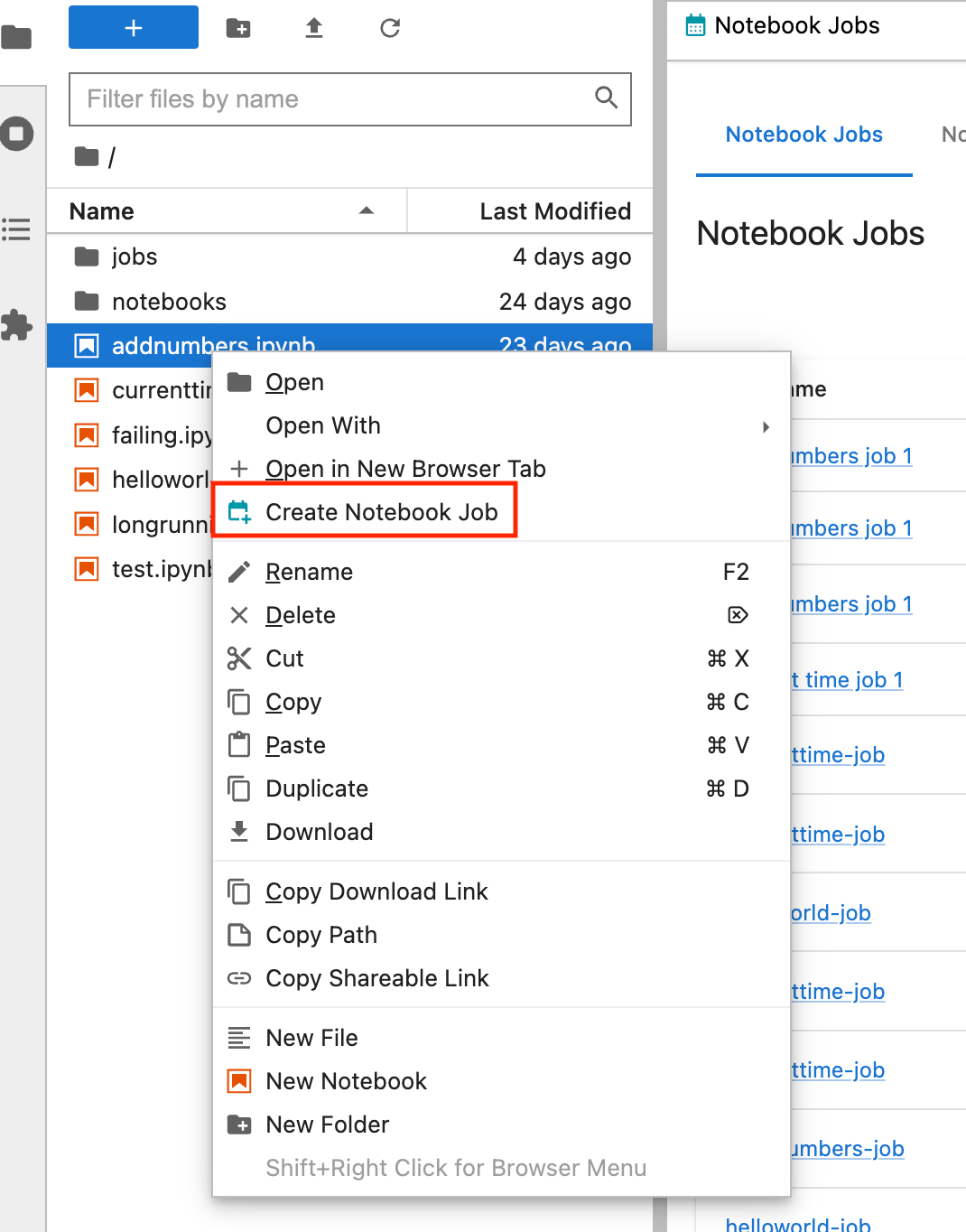
Introducing Jupyter Scheduler. The Open Source Jupyter team at AWS is… | by Jason Weill | Jupyter Blog

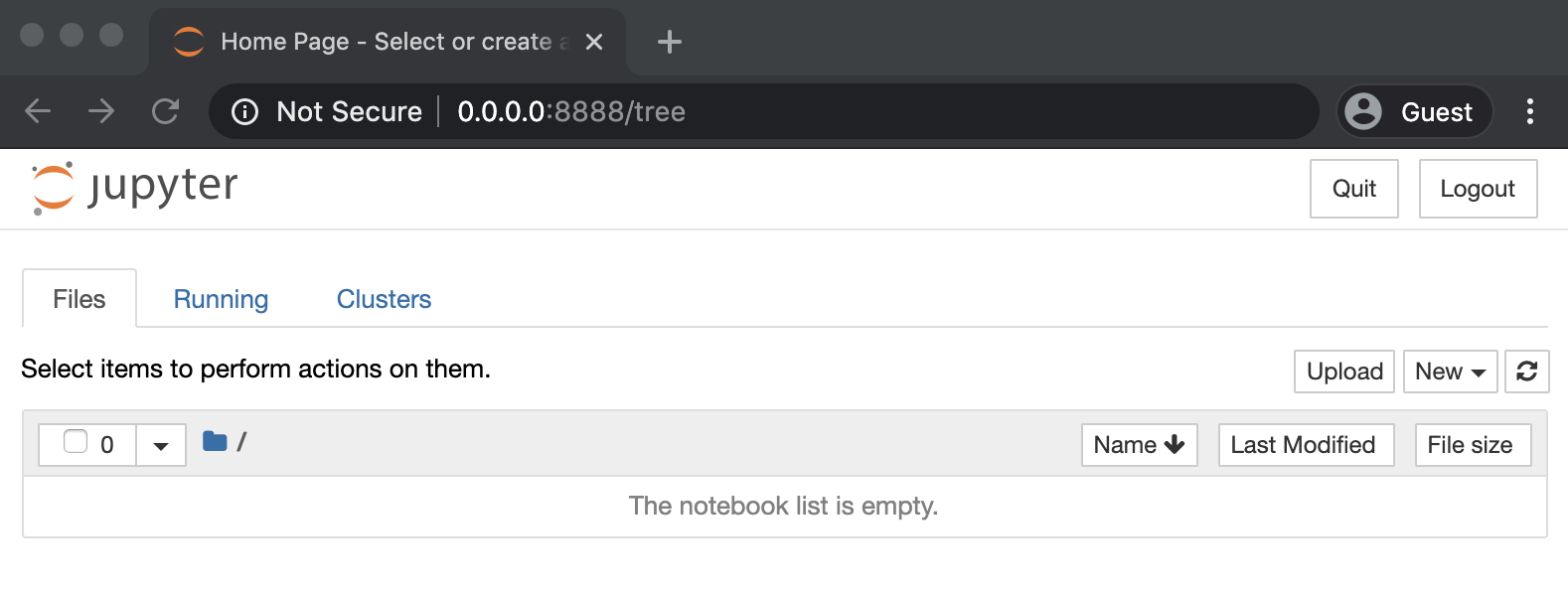
Not able to load the Jupyter notebook UI page Getting Error "EvalError" - JupyterHub - Jupyter Community Forum